Szablon: Web banip: Różnice pomiędzy wersjami
| Linia 120: | Linia 120: | ||
|- | |- | ||
| Trigger Delay | | Trigger Delay | ||
| | | range from 1 to 120, default: 5 | ||
| Additional trigger delay in seconds before banIP processing begins. | | Additional trigger delay in seconds before banIP processing begins. | ||
|- | |- | ||
| Download Queue | | Download Queue | ||
| | | 1, 2, 4, 8, 16 or 32, default: 4 | ||
| Size of the download queue for download processing in parallel. | | Size of the download queue for download processing in parallel. | ||
|- | |- | ||
| Linia 140: | Linia 140: | ||
|- | |- | ||
| Download Utility | | Download Utility | ||
| | | uclient-fetch, wget, curl or aria2c, default: none | ||
| List of supported and fully pre-configured download utilities. | | List of supported and fully pre-configured download utilities. | ||
|- | |- | ||
| Download Insecure | | Download Insecure | ||
| | | On/Off, default: Off | ||
| Don't check SSL server certificates during download. | | Don't check SSL server certificates during download. | ||
|- | |- | ||
| Linia 153: | Linia 153: | ||
===Advanced Chain Settings==== | ===Advanced Chain Settings==== | ||
<b>Advanced Chain Settings</b> tab is divided into three parts: Individual IPSet Settings, IPv4 Chains and IPv6 Chains which are described in the tables below. Note: Changes on this tab needs a full banIP service restart to take effect. | |||
{| class="wikitable" | |||
|- | |||
! Name | |||
! Value | |||
! Description | |||
|- | |||
| Global IPSet Type | |||
| src_dst, src or dst, default: src+dst | |||
| Set the global IPset type default, to block incoming (SRC) and/or outgoing (DST) packets. | |||
|- | |||
| SRC Target | |||
| DROP or REJECT, default: DROP | |||
| Set the firewall target for all SRC related rules. | |||
|- | |||
| DST Target | |||
| REJECT or DROP, default: REJECT | |||
| Set the firewall target for all DST related rules. | |||
|- | |||
| Maclist Timeout | |||
| 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | |||
| Set the maclist IPSet timeout. | |||
|- | |||
| Whitelist Timeout | |||
| 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | |||
| Set the whitelist IPSet timeout. | |||
|- | |||
| Blacklist Timeout | |||
| 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | |||
| Set the blacklist IPSet timeout. | |||
|- | |||
| SRC IPSet Type | |||
| | |||
| Set individual SRC type per IPset to block only incoming packets. | |||
|- | |||
| DST IPSet Type | |||
| | |||
| Set individual DST type per IPset to block only outgoing packets. | |||
|- | |||
| SRC+DST IPSet Type | |||
| | |||
| Set individual SRC+DST type per IPset to block incoming and outgoing packets. | |||
|- | |||
| LAN Input (IPv4 Chains) | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_lan_rule'. | |||
|- | |||
| LAN Forward | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_lan_rule'. | |||
|- | |||
| WAN Input | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_wan_rule'. | |||
|- | |||
| WAN Forward | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_wan_rule'. | |||
|- | |||
| LAN Input (IPv6 Chains) | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_lan_rule'. | |||
|- | |||
| LAN Forward | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_lan_rule'. | |||
|- | |||
| WAN Input | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_wan_rule'. | |||
|- | |||
| WAN Forward | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_wan_rule'. | |||
|} | |||
===Advanced Log Settings==== | ===Advanced Log Settings==== | ||
Wersja z 11:18, 27 maj 2022
The banIP page of {{{model}}} router is used to configure banIP package to block ip addresses/subnets via IPSet.
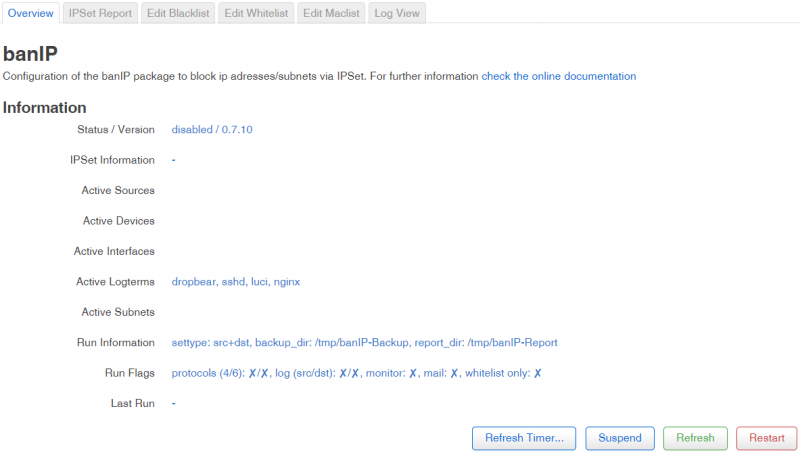
Overview
Information
banIP package details can be found in Information section. You can refresh timer, suspend, refresh or restart the package using the corresponding buttons.
In Services part user can manage the DDNS services providers.
| Name | Value | Description |
|---|---|---|
| Status / Version | Package status and version | |
| IPSet Information | ||
| Active Sources | ||
| Active Devices | ||
| Active Interfaces | ||
| Active Logterms | ||
| Active Subnets | ||
| Run Information | ||
| Run Flags | ||
| Last Run |
Settings
General Settings=
| Name | Value | Description |
|---|---|---|
| Enabled | On/Off, default: Off | Enable the banIP service. |
| Startup Trigger Interface | unspecified, dhcp, gsm or lan, default: gsm | List of available network interfaces to trigger the banIP start. |
| Auto Detection | On/Off, default: On | Detect relevant network interfaces, devices, subnets and protocols automatically. |
| Log Monitor | On/Off, default: Off | Starts a small log monitor in the background to block suspicious SSH/LuCI login attempts. |
| Enable SRC logging | On/Off, default: On | Log suspicious incoming packets - usually dropped. |
| Enable DST logging | On/Off, default: Off | Log suspicious outgoing packets - usually rejected. Logging such packets may cause an increase in latency due to it requiring additional system resources. |
| Whitelist Only | On/Off, default: Off | Restrict the internet access from/to a small number of secure websites/IPs and block access from/to the rest of the internet. |
| E-Mail Notification | On/Off, default: Off | Send banIP related notification e-mails. This needs the installation and setup of the additional 'msmtp' package. |
Additional Settings=
| Name | Value | Description |
|---|---|---|
| Verbose Debug Logging | On/Off, default: Off | Enable verbose debug logging in case of any processing errors. |
| Service Priority | Highest Priority, High Priority, Normal Priority, Less Priority or Least Priority, default: Normal Priority | The selected priority will be used for banIP background processing. This change requires a full banIP service restart to take effect. |
| Trigger Delay | range from 1 to 120, default: 5 | Additional trigger delay in seconds before banIP processing begins. |
| Download Queue | 1, 2, 4, 8, 16 or 32, default: 4 | Size of the download queue for download processing in parallel. |
| Base Temp Directory | Base Temp Directory used for all banIP related runtime operations. | |
| Backup Directory | Target directory for compressed source list backups. | |
| Report Directory | Target directory for IPSet related report files. | |
| Download Utility | uclient-fetch, wget, curl or aria2c, default: none | List of supported and fully pre-configured download utilities. |
| Download Insecure | On/Off, default: Off | Don't check SSL server certificates during download. |
| Download Parameters | Manually override the pre-configured download options for the selected download utility. |
Advanced Chain Settings=
Advanced Chain Settings tab is divided into three parts: Individual IPSet Settings, IPv4 Chains and IPv6 Chains which are described in the tables below. Note: Changes on this tab needs a full banIP service restart to take effect.
| Name | Value | Description |
|---|---|---|
| Global IPSet Type | src_dst, src or dst, default: src+dst | Set the global IPset type default, to block incoming (SRC) and/or outgoing (DST) packets. |
| SRC Target | DROP or REJECT, default: DROP | Set the firewall target for all SRC related rules. |
| DST Target | REJECT or DROP, default: REJECT | Set the firewall target for all DST related rules. |
| Maclist Timeout | 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | Set the maclist IPSet timeout. |
| Whitelist Timeout | 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | Set the whitelist IPSet timeout. |
| Blacklist Timeout | 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | Set the blacklist IPSet timeout. |
| SRC IPSet Type | Set individual SRC type per IPset to block only incoming packets. | |
| DST IPSet Type | Set individual DST type per IPset to block only outgoing packets. | |
| SRC+DST IPSet Type | Set individual SRC+DST type per IPset to block incoming and outgoing packets. | |
| LAN Input (IPv4 Chains) | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_lan_rule'. | |
| LAN Forward | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_lan_rule'. | |
| WAN Input | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_wan_rule'. | |
| WAN Forward | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_wan_rule'. | |
| LAN Input (IPv6 Chains) | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_lan_rule'. | |
| LAN Forward | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_lan_rule'. | |
| WAN Input | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_wan_rule'. | |
| WAN Forward | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_wan_rule'. |
Advanced Log Settings=
Advanced E-Mail Settings=
Blocklist Sources=
IPSet Report
This tab shows the last generated IPSet Report. Press the Refresh button to get a current one. To Search the active banIP-related IPSets for a specific IP, CIDR or MAC address press IPSet Querry button.
| Name | Value | Description |
|---|---|---|
| Timestamp | ||
| Number of all IPSets | number | |
| Number of all entries | number | |
| Number of IP entries | number | |
| Number of CIDR entries | number | |
| Number of MAC entries | number | |
| Number of accessed entries | number |
Edit Blacklist
This is the local banIP blacklist to always-deny certain IP/CIDR addresses. Note: add only one IPv4 address, IPv6 address or domain name per line. Comments introduced with '#' are allowed - wildcards and regex are not.
Edit Whitelist
This is the local banIP whitelist to always allow certain IP/CIDR addresses. Note: add only one IPv4 address, IPv6 address or domain name per line. Comments introduced with '#' are allowed - wildcards and regex are not.
Edit Maclist
This is the local banIP maclist to always-allow certain MAC addresses. Note: add only one MAC address per line. Comments introduced with '#' are allowed - domains, wildcards and regex are not.
Log View
The syslog output, pre-filtered for banIP related messages only.
[[Category:{{{model}}} User Manual]]