Szablon: Web ipsec: Różnice pomiędzy wersjami
Z Elproma Wiki Knowledge Base
| (Nie pokazano 3 pośrednich wersji utworzonych przez tego samego użytkownika) | |||
| Linia 1: | Linia 1: | ||
The <b> | The <b>IPSec</b> page of {{{model}}} {{{type}}} is used to configure IPSec tunnel. | ||
==Tunnels Configuration== | ==Tunnels Configuration== | ||
In <b>Tunnels Configuration</b> part you can add, edit or delete | In <b>Tunnels Configuration</b> part you can add, edit or delete IPSec tunnel. To add new tunnel use Add button. | ||
[[File:web_vpnipsec.png|800px|border|class=tlt-border]] | [[File:web_vpnipsec.png|800px|border|class=tlt-border]] | ||
| Linia 89: | Linia 89: | ||
[[File:web_vpnipseca.png|800px|border|class=tlt-border]] | [[File:web_vpnipseca.png|800px|border|class=tlt-border]] | ||
== | ==IPSec Configuration== | ||
[[File:web_vpnipsecconf.png|800px|border|class=tlt-border]] | [[File:web_vpnipsecconf.png|800px|border|class=tlt-border]] | ||
| Linia 181: | Linia 181: | ||
|} | |} | ||
[[File:web_vpnipsecconfa.png| | [[File:web_vpnipsecconfa.png|800px|border|class=tlt-border]] | ||
===Crypto Proposals=== | |||
{| class="wikitable" | |||
|- | |||
! Name | |||
! Value | |||
! Description | |||
|- | |||
| Name | |||
| string | |||
| Name of proposal | |||
|- | |||
| encryption_method | |||
| aes128, aes192, aes256 or 3des | |||
| | |||
|- | |||
| hash_algorithm | |||
| md5, sha1, sha2 or 3des | |||
| | |||
|- | |||
| dh_group | |||
| modp768, modp1024 or modp2048 | |||
| | |||
|- | |||
| prf_algorithm | |||
| prfmd5, prfsha1 or prfsha256 | |||
| | |||
|} | |||
[[File:web_vpnipseccrypto.png|800px|border|class=tlt-border]] | |||
[[Category:{{{model}}} User Manual]] | [[Category:{{{model}}} User Manual]] | ||
Aktualna wersja na dzień 15:12, 26 kwi 2024
The IPSec page of {{{model}}} {{{type}}} is used to configure IPSec tunnel.
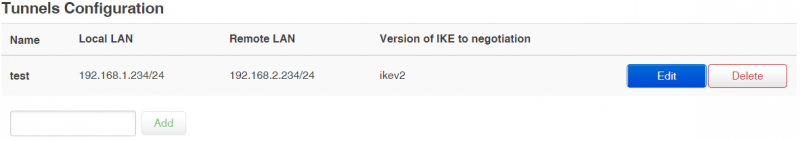
Tunnels Configuration
In Tunnels Configuration part you can add, edit or delete IPSec tunnel. To add new tunnel use Add button.
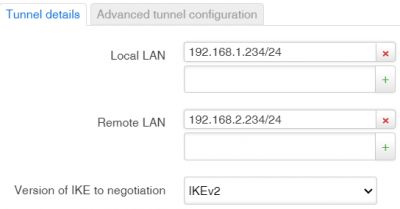
Tunnel details
| Name | Value | Description |
|---|---|---|
| Local LAN | ||
| Remote LAN | ||
| Version of IKE to negotiation | IKEv2, IKEv1 or IKEv1 + IKEv2. Default: IKEv2 |
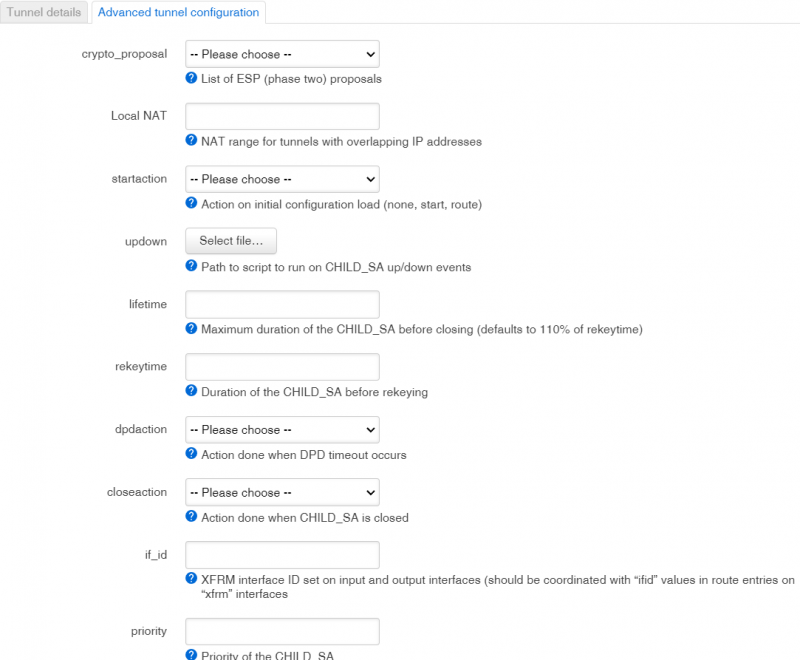
Advanced tunnel configuration
| Name | Value | Description |
|---|---|---|
| crypto_proposal | list | List of ESP (phase two) proposals |
| Local NAT | IPv4 in CIDR format | NAT range for tunnels with overlapping IP addresses |
| startaction | route, start or none | Action on initial configuration load (none, start, route) |
| updown | file | Path to script to run on CHILD_SA up/down events |
| lifetime | Maximum duration of the CHILD_SA before closing (defaults to 110% of rekeytime) | |
| rekeytime | Duration of the CHILD_SA before rekeying | |
| dpdaction | none, clear, hold, restart, trap or start | Action done when DPD timeout occurs |
| closeaction | add, route, start, none or trap | Action done when CHILD_SA is closed |
| if_id | XFRM interface ID set on input and output interfaces (should be coordinated with “ifid” values in route entries on “xfrm” interfaces | |
| priority | integer equal or higher than 0 | Priority of the CHILD_SA |
| ipcomp | On/Off, default: Off | Enable ipcomp compression |
| hw_offload | On/Off, default: Off | Enable H/W offload |
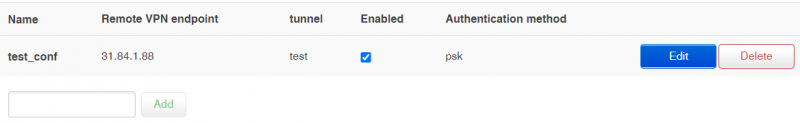
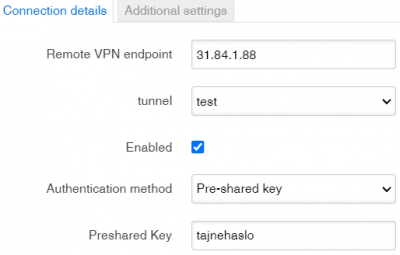
IPSec Configuration
Connection details
| Name | Value | Description |
|---|---|---|
| Remote VPN endpoint | ||
| tunnel | ||
| Enabled | ||
| Authentication method | Pre-shared key or X.509. Default: Pre-shared key | |
| Preshared Key |
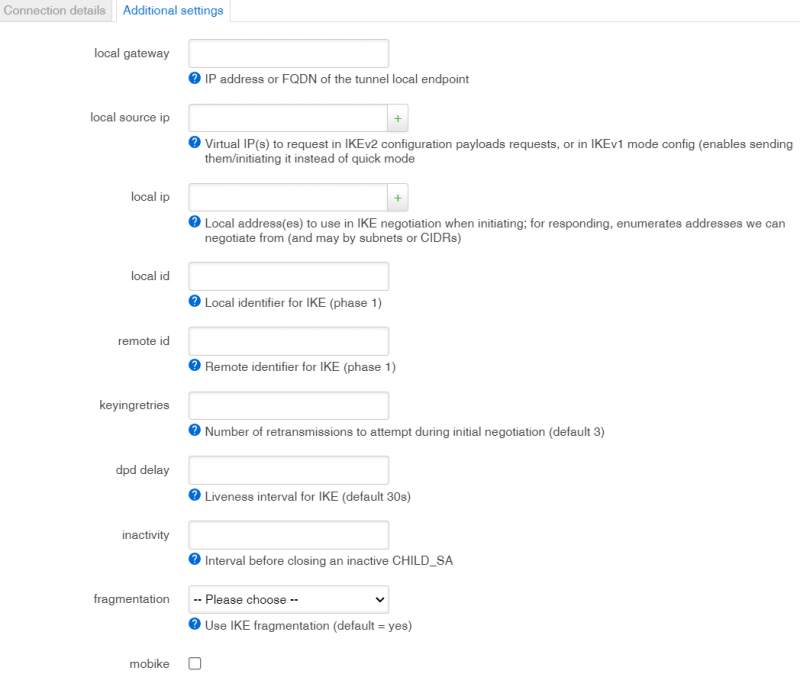
Additional settings
| Name | Value | Description |
|---|---|---|
| local gateway | IP address or FQDN of the tunnel local endpoint | |
| local source ip | Virtual IP(s) to request in IKEv2 configuration payloads requests, or in IKEv1 mode config (enables sending them/initiating it instead of quick mode | |
| local ip | Local address(es) to use in IKE negotiation when initiating; for responding, enumerates addresses we can negotiate from (and may by subnets or CIDRs) | |
| local id | Local identifier for IKE (phase 1) | |
| remote id | Remote identifier for IKE (phase 1) | |
| keyingretries | Number of retransmissions to attempt during initial negotiation (default 3) | |
| dpd delay | Liveness interval for IKE (default 30s) | |
| inactivity | Interval before closing an inactive CHILD_SA | |
| fragmentation | yes, accept, force or no. Default: yes | Use IKE fragmentation |
| mobike | Enable MOBIKE on IKEv2 (default = yes) | |
| rekeytime | IKEv2 interval to refresh keying material; also used to compute lifetime | |
| overtime | Limit on time to complete rekeying/reauthentication (defaults to 10% of rekeytime) |
Crypto Proposals
| Name | Value | Description |
|---|---|---|
| Name | string | Name of proposal |
| encryption_method | aes128, aes192, aes256 or 3des | |
| hash_algorithm | md5, sha1, sha2 or 3des | |
| dh_group | modp768, modp1024 or modp2048 | |
| prf_algorithm | prfmd5, prfsha1 or prfsha256 |
[[Category:{{{model}}} User Manual]]