Szablon: Web banip: Różnice pomiędzy wersjami
(Utworzono nową stronę "The <b>banIP</b> page of {{{model}}} router is used to configure banIP package to block ip addresses/subnets via IPSet. ==Overview== ===Information=== banIP package details can be found in <b>Information</b> section. You can refresh timer, suspend, refresh or restart the package using the corresponding buttons. 800px|border|class=tlt-border In <b>Services</b> part user can manage the DDNS services providers. {| class="wikitable"…") |
|||
| (Nie pokazano 5 pośrednich wersji utworzonych przez tego samego użytkownika) | |||
| Linia 1: | Linia 1: | ||
The <b>banIP</b> page of {{{model}}} | The <b>banIP</b> page of {{{model}}} {{{type}}} is used to configure banIP package to block ip addresses/subnets via IPSet. | ||
==Overview== | ==Overview== | ||
| Linia 6: | Linia 6: | ||
banIP package details can be found in <b>Information</b> section. You can refresh timer, suspend, refresh or restart the package using the corresponding buttons. | banIP package details can be found in <b>Information</b> section. You can refresh timer, suspend, refresh or restart the package using the corresponding buttons. | ||
{| class="wikitable" | {| class="wikitable" | ||
| Linia 57: | Linia 53: | ||
| | | | ||
|} | |} | ||
[[File:web_servicesbanipinformation.png|800px|frameless|class=tlt-border]] | |||
===Settings=== | |||
====General Settings==== | |||
{| class="wikitable" | |||
|- | |||
! Name | |||
! Value | |||
! Description | |||
|- | |||
| Enabled | |||
| On/Off, default: Off | |||
| Enable the banIP service. | |||
|- | |||
| Startup Trigger Interface | |||
| unspecified, dhcp, gsm or lan, default: gsm | |||
| List of available network interfaces to trigger the banIP start. | |||
|- | |||
| Auto Detection | |||
| On/Off, default: On | |||
| Detect relevant network interfaces, devices, subnets and protocols automatically. | |||
|- | |||
| Log Monitor | |||
| On/Off, default: Off | |||
| Starts a small log monitor in the background to block suspicious SSH/LuCI login attempts. | |||
|- | |||
| Enable SRC logging | |||
| On/Off, default: On | |||
| Log suspicious incoming packets - usually dropped. | |||
|- | |||
| Enable DST logging | |||
| On/Off, default: Off | |||
| Log suspicious outgoing packets - usually rejected. Logging such packets may cause an increase in latency due to it requiring additional system resources. | |||
|- | |||
| Whitelist Only | |||
| On/Off, default: Off | |||
| Restrict the internet access from/to a small number of secure websites/IPs and block access from/to the rest of the internet. | |||
|- | |||
| E-Mail Notification | |||
| On/Off, default: Off | |||
| Send banIP related notification e-mails. This needs the installation and setup of the additional 'msmtp' package. | |||
|} | |||
[[File:web_servicesbanipgeneralsettings.png|800px|frameless|class=tlt-border]] | |||
====Additional Settings==== | |||
{| class="wikitable" | |||
|- | |||
! Name | |||
! Value | |||
! Description | |||
|- | |||
| Verbose Debug Logging | |||
| On/Off, default: Off | |||
| Enable verbose debug logging in case of any processing errors. | |||
|- | |||
| Service Priority | |||
| Highest Priority, High Priority, Normal Priority, Less Priority or Least Priority, default: Normal Priority | |||
| The selected priority will be used for banIP background processing. This change requires a full banIP service restart to take effect. | |||
|- | |||
| Trigger Delay | |||
| range from 1 to 120, default: 5 | |||
| Additional trigger delay in seconds before banIP processing begins. | |||
|- | |||
| Download Queue | |||
| 1, 2, 4, 8, 16 or 32, default: 4 | |||
| Size of the download queue for download processing in parallel. | |||
|- | |||
| Base Temp Directory | |||
| | |||
| Base Temp Directory used for all banIP related runtime operations. | |||
|- | |||
| Backup Directory | |||
| | |||
| Target directory for compressed source list backups. | |||
|- | |||
| Report Directory | |||
| | |||
| Target directory for IPSet related report files. | |||
|- | |||
| Download Utility | |||
| uclient-fetch, wget, curl or aria2c, default: none | |||
| List of supported and fully pre-configured download utilities. | |||
|- | |||
| Download Insecure | |||
| On/Off, default: Off | |||
| Don't check SSL server certificates during download. | |||
|- | |||
| Download Parameters | |||
| | |||
| Manually override the pre-configured download options for the selected download utility. | |||
|} | |||
[[File:web_servicesbanipadditionalsettings.png|800px|frameless|class=tlt-border]] | |||
====Advanced Chain Settings==== | |||
<b>Advanced Chain Settings</b> tab is divided into three parts: Individual IPSet Settings, IPv4 Chains and IPv6 Chains which are described in the table below. Note: Changes on this tab needs a full banIP service restart to take effect. | |||
{| class="wikitable" | |||
|- | |||
! Name | |||
! Value | |||
! Description | |||
|- | |||
| Global IPSet Type | |||
| src_dst, src or dst, default: src+dst | |||
| Set the global IPset type default, to block incoming (SRC) and/or outgoing (DST) packets. | |||
|- | |||
| SRC Target | |||
| DROP or REJECT, default: DROP | |||
| Set the firewall target for all SRC related rules. | |||
|- | |||
| DST Target | |||
| REJECT or DROP, default: REJECT | |||
| Set the firewall target for all DST related rules. | |||
|- | |||
| Maclist Timeout | |||
| 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | |||
| Set the maclist IPSet timeout. | |||
|- | |||
| Whitelist Timeout | |||
| 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | |||
| Set the whitelist IPSet timeout. | |||
|- | |||
| Blacklist Timeout | |||
| 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | |||
| Set the blacklist IPSet timeout. | |||
|- | |||
| SRC IPSet Type | |||
| | |||
| Set individual SRC type per IPset to block only incoming packets. | |||
|- | |||
| DST IPSet Type | |||
| | |||
| Set individual DST type per IPset to block only outgoing packets. | |||
|- | |||
| SRC+DST IPSet Type | |||
| | |||
| Set individual SRC+DST type per IPset to block incoming and outgoing packets. | |||
|- | |||
| LAN Input (IPv4 Chains) | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_lan_rule'. | |||
|- | |||
| LAN Forward | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_lan_rule'. | |||
|- | |||
| WAN Input | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_wan_rule'. | |||
|- | |||
| WAN Forward | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_wan_rule'. | |||
|- | |||
| LAN Input (IPv6 Chains) | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_lan_rule'. | |||
|- | |||
| LAN Forward | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_lan_rule'. | |||
|- | |||
| WAN Input | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_wan_rule'. | |||
|- | |||
| WAN Forward | |||
| | |||
| Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_wan_rule'. | |||
|} | |||
[[File:web_servicesbanipadvancedchainsettings.png|800px|frameless|class=tlt-border]] | |||
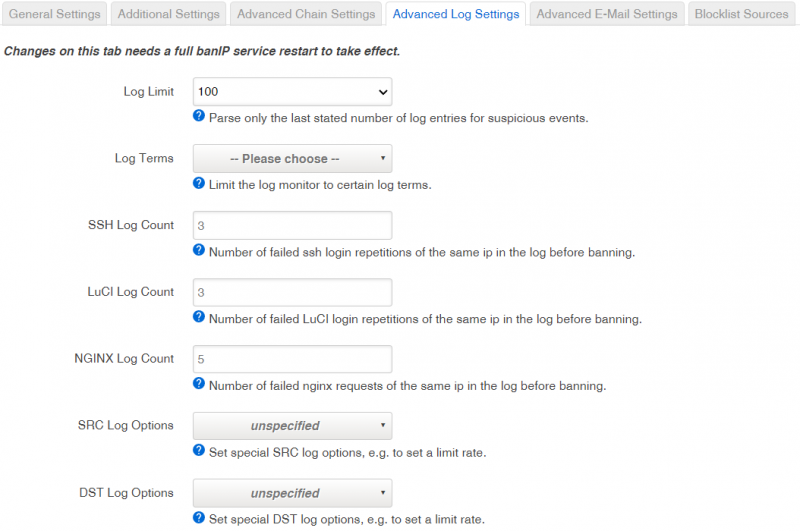
====Advanced Log Settings==== | |||
Note: Changes on this tab needs a full banIP service restart to take effect. | |||
{| class="wikitable" | |||
|- | |||
! Name | |||
! Value | |||
! Description | |||
|- | |||
| Log Limit | |||
| 50, 100, 250 or 500, default: 100 | |||
| Parse only the last stated number of log entries for suspicious events. | |||
|- | |||
| Log Terms | |||
| dropbear, sshd, luci or nginx, default: none | |||
| Limit the log monitor to certain log terms. | |||
|- | |||
| SSH Log Count | |||
| range from 1 to 10, default: 3 | |||
| Number of failed ssh login repetitions of the same ip in the log before banning. | |||
|- | |||
| LuCI Log Count | |||
|range from 1 to 10, default: 3 | |||
| Number of failed LuCI login repetitions of the same ip in the log before banning. | |||
|- | |||
| NGINX Log Count | |||
|range from 1 to 20, default: 5 | |||
| Number of failed nginx requests of the same ip in the log before banning. | |||
|- | |||
| SRC Log Options | |||
| -m limit --limit 2/sec (default), -m limit --limit 10/sec or custom, default: none | |||
| Set special SRC log options, e.g. to set a limit rate. | |||
|- | |||
| DST Log Options | |||
| -m limit --limit 2/sec (default), -m limit --limit 10/sec or custom, default: none | |||
| Set special DST log options, e.g. to set a limit rate. | |||
|} | |||
[[File:web_servicesbanipadvancedlogsettings.png|800px|frameless|class=tlt-border]] | |||
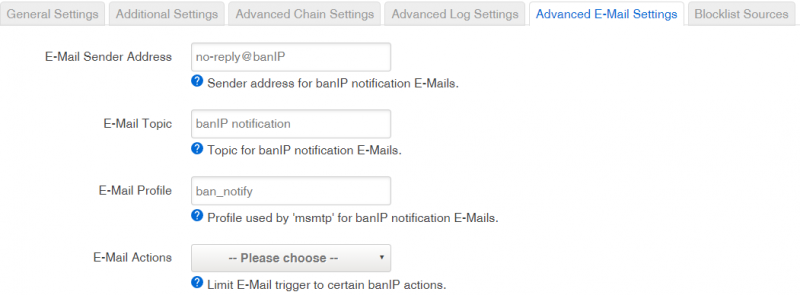
====Advanced E-Mail Settings==== | |||
{| class="wikitable" | |||
|- | |||
! Name | |||
! Value | |||
! Description | |||
|- | |||
| E-Mail Sender Address | |||
| | |||
| Sender address for banIP notification E-Mails. | |||
|- | |||
| E-Mail Topic | |||
| string | |||
| Topic for banIP notification E-Mails. | |||
|- | |||
| E-Mail Profile | |||
| string | |||
| Profile used by 'msmtp' for banIP notification E-Mails. | |||
|- | |||
| E-Mail Actions | |||
| start, reload, restart or refresh, default: none | |||
| Limit E-Mail trigger to certain banIP actions. | |||
|} | |||
[[File:web_servicesbanipadvancedemailsettings.png|800px|frameless|class=tlt-border]] | |||
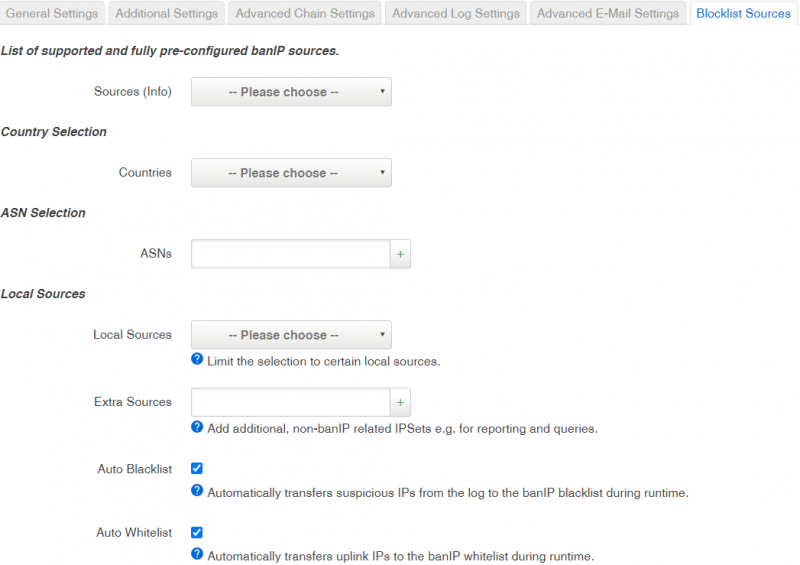
====Blocklist Sources==== | |||
In <b>Blocklist Sources</b> tab user can manage supported and fully pre-configured banIP sources. Section is divided into three parts: Country Selection, ASN Selection and Local Sources which are described in the table below. | |||
{| class="wikitable" | |||
|- | |||
! Name | |||
! Value | |||
! Description | |||
|- | |||
| Countries | |||
| | |||
| | |||
|- | |||
| ASNs | |||
| | |||
| | |||
|- | |||
| Local Sources | |||
| | |||
| | |||
|- | |||
| Extra Sources | |||
| | |||
| | |||
|- | |||
| Auto Blacklist | |||
| | |||
| | |||
|- | |||
| Auto Whitelist | |||
| | |||
| | |||
|} | |||
[[File:web_servicesbanipblocklistsources.png|800px|frameless|class=tlt-border]] | |||
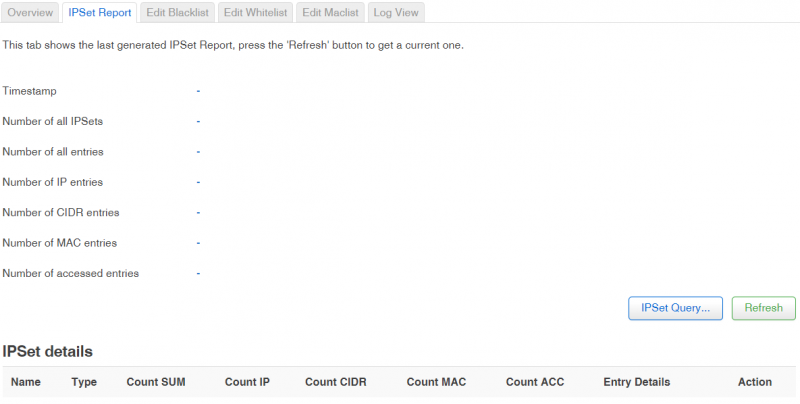
==IPSet Report== | ==IPSet Report== | ||
This tab shows the last generated IPSet Report. Press the | This tab shows the last generated IPSet Report. Press the Refresh button to get a current one. To Search the active banIP-related IPSets for a specific IP, CIDR or MAC address press IPSet Querry button. | ||
{| class="wikitable" | {| class="wikitable" | ||
| Linia 73: | Linia 353: | ||
|- | |- | ||
| Number of all IPSets | | Number of all IPSets | ||
| | | number | ||
| | | | ||
|- | |- | ||
| Number of all entries | | Number of all entries | ||
| | | number | ||
| | | | ||
|- | |- | ||
| Number of IP entries | | Number of IP entries | ||
| | | number | ||
| | | | ||
|- | |- | ||
| Number of CIDR entries | | Number of CIDR entries | ||
| | | number | ||
| | | | ||
|- | |- | ||
| Number of MAC entries | | Number of MAC entries | ||
| | | number | ||
| | | | ||
|- | |- | ||
| Number of accessed entries | | Number of accessed entries | ||
| | | number | ||
| | | | ||
|} | |} | ||
[[File:web_servicesbanipipsetreport.png|800px|frameless|class=tlt-border]] | |||
==Edit Blacklist== | ==Edit Blacklist== | ||
This is the local banIP blacklist to always-deny certain IP/CIDR addresses. | |||
Note: add only one IPv4 address, IPv6 address or domain name per line. Comments introduced with '#' are allowed - wildcards and regex are not. | |||
==Edit Whitelist== | ==Edit Whitelist== | ||
This is the local banIP whitelist to always allow certain IP/CIDR addresses. | |||
Note: add only one IPv4 address, IPv6 address or domain name per line. Comments introduced with '#' are allowed - wildcards and regex are not. | |||
==Edit Maclist== | ==Edit Maclist== | ||
This is the local banIP maclist to always-allow certain MAC addresses. | |||
Note: add only one MAC address per line. Comments introduced with '#' are allowed - domains, wildcards and regex are not. | |||
==Log View== | ==Log View== | ||
The syslog output, pre-filtered for banIP related messages only. | |||
[[Category:{{{model}}} User Manual]] | [[Category:{{{model}}} User Manual]] | ||
Aktualna wersja na dzień 10:09, 26 kwi 2024
The banIP page of {{{model}}} {{{type}}} is used to configure banIP package to block ip addresses/subnets via IPSet.
Overview
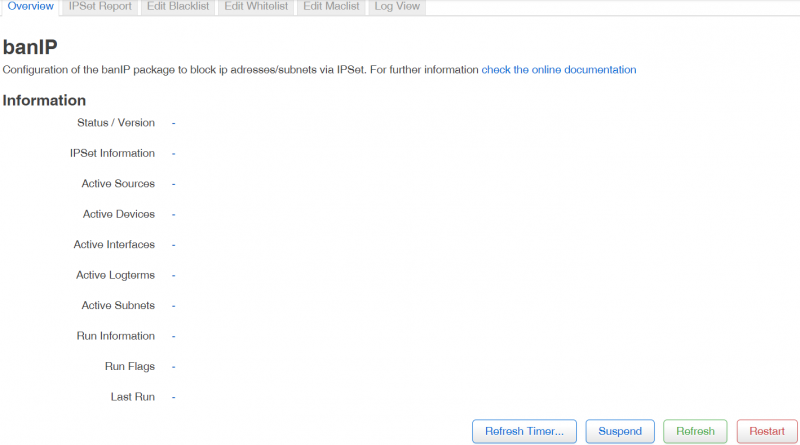
Information
banIP package details can be found in Information section. You can refresh timer, suspend, refresh or restart the package using the corresponding buttons.
| Name | Value | Description |
|---|---|---|
| Status / Version | Package status and version | |
| IPSet Information | ||
| Active Sources | ||
| Active Devices | ||
| Active Interfaces | ||
| Active Logterms | ||
| Active Subnets | ||
| Run Information | ||
| Run Flags | ||
| Last Run |
Settings
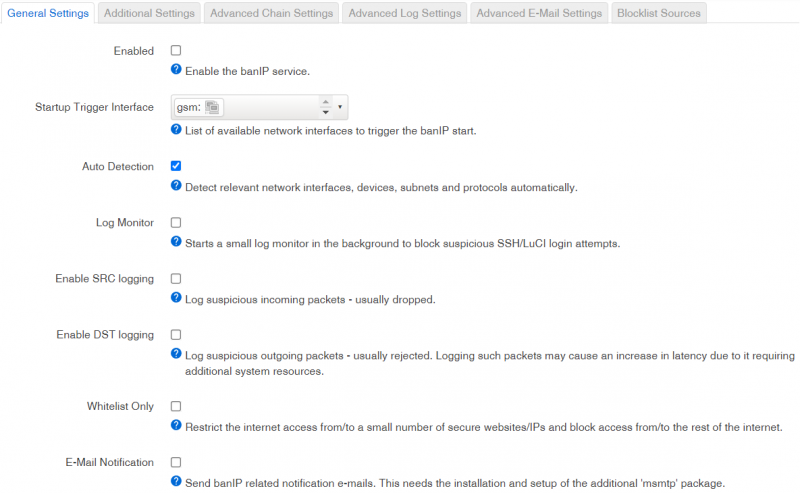
General Settings
| Name | Value | Description |
|---|---|---|
| Enabled | On/Off, default: Off | Enable the banIP service. |
| Startup Trigger Interface | unspecified, dhcp, gsm or lan, default: gsm | List of available network interfaces to trigger the banIP start. |
| Auto Detection | On/Off, default: On | Detect relevant network interfaces, devices, subnets and protocols automatically. |
| Log Monitor | On/Off, default: Off | Starts a small log monitor in the background to block suspicious SSH/LuCI login attempts. |
| Enable SRC logging | On/Off, default: On | Log suspicious incoming packets - usually dropped. |
| Enable DST logging | On/Off, default: Off | Log suspicious outgoing packets - usually rejected. Logging such packets may cause an increase in latency due to it requiring additional system resources. |
| Whitelist Only | On/Off, default: Off | Restrict the internet access from/to a small number of secure websites/IPs and block access from/to the rest of the internet. |
| E-Mail Notification | On/Off, default: Off | Send banIP related notification e-mails. This needs the installation and setup of the additional 'msmtp' package. |
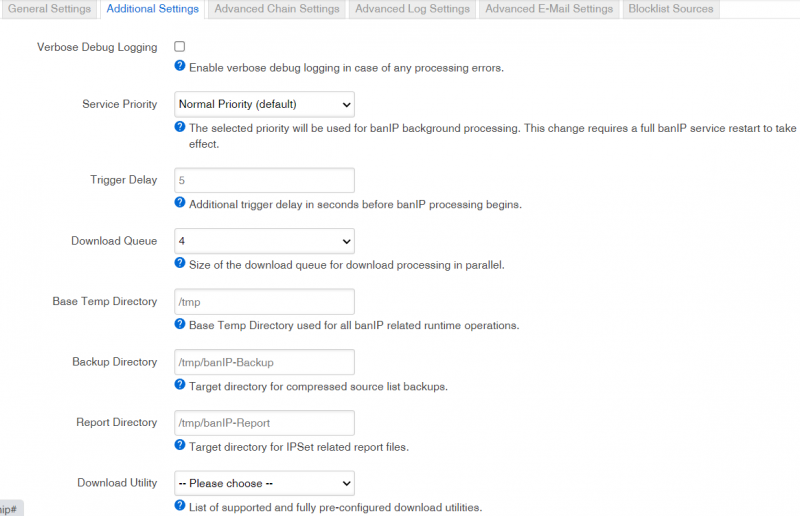
Additional Settings
| Name | Value | Description |
|---|---|---|
| Verbose Debug Logging | On/Off, default: Off | Enable verbose debug logging in case of any processing errors. |
| Service Priority | Highest Priority, High Priority, Normal Priority, Less Priority or Least Priority, default: Normal Priority | The selected priority will be used for banIP background processing. This change requires a full banIP service restart to take effect. |
| Trigger Delay | range from 1 to 120, default: 5 | Additional trigger delay in seconds before banIP processing begins. |
| Download Queue | 1, 2, 4, 8, 16 or 32, default: 4 | Size of the download queue for download processing in parallel. |
| Base Temp Directory | Base Temp Directory used for all banIP related runtime operations. | |
| Backup Directory | Target directory for compressed source list backups. | |
| Report Directory | Target directory for IPSet related report files. | |
| Download Utility | uclient-fetch, wget, curl or aria2c, default: none | List of supported and fully pre-configured download utilities. |
| Download Insecure | On/Off, default: Off | Don't check SSL server certificates during download. |
| Download Parameters | Manually override the pre-configured download options for the selected download utility. |
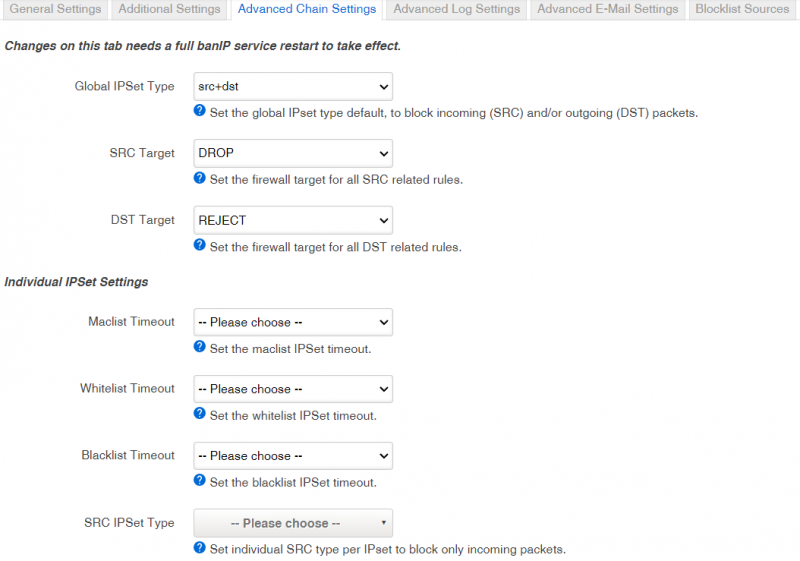
Advanced Chain Settings
Advanced Chain Settings tab is divided into three parts: Individual IPSet Settings, IPv4 Chains and IPv6 Chains which are described in the table below. Note: Changes on this tab needs a full banIP service restart to take effect.
| Name | Value | Description |
|---|---|---|
| Global IPSet Type | src_dst, src or dst, default: src+dst | Set the global IPset type default, to block incoming (SRC) and/or outgoing (DST) packets. |
| SRC Target | DROP or REJECT, default: DROP | Set the firewall target for all SRC related rules. |
| DST Target | REJECT or DROP, default: REJECT | Set the firewall target for all DST related rules. |
| Maclist Timeout | 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | Set the maclist IPSet timeout. |
| Whitelist Timeout | 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | Set the whitelist IPSet timeout. |
| Blacklist Timeout | 30 minutes, 1 hour, 6 hours, 12 hours or 24 hours, default: none | Set the blacklist IPSet timeout. |
| SRC IPSet Type | Set individual SRC type per IPset to block only incoming packets. | |
| DST IPSet Type | Set individual DST type per IPset to block only outgoing packets. | |
| SRC+DST IPSet Type | Set individual SRC+DST type per IPset to block incoming and outgoing packets. | |
| LAN Input (IPv4 Chains) | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_lan_rule'. | |
| LAN Forward | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_lan_rule'. | |
| WAN Input | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_wan_rule'. | |
| WAN Forward | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_wan_rule'. | |
| LAN Input (IPv6 Chains) | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_lan_rule'. | |
| LAN Forward | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_lan_rule'. | |
| WAN Input | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'input_wan_rule'. | |
| WAN Forward | Assign one or more relevant firewall chains to banIP. The default chain used by banIP is 'forwarding_wan_rule'. |
Advanced Log Settings
Note: Changes on this tab needs a full banIP service restart to take effect.
| Name | Value | Description |
|---|---|---|
| Log Limit | 50, 100, 250 or 500, default: 100 | Parse only the last stated number of log entries for suspicious events. |
| Log Terms | dropbear, sshd, luci or nginx, default: none | Limit the log monitor to certain log terms. |
| SSH Log Count | range from 1 to 10, default: 3 | Number of failed ssh login repetitions of the same ip in the log before banning. |
| LuCI Log Count | range from 1 to 10, default: 3 | Number of failed LuCI login repetitions of the same ip in the log before banning. |
| NGINX Log Count | range from 1 to 20, default: 5 | Number of failed nginx requests of the same ip in the log before banning. |
| SRC Log Options | -m limit --limit 2/sec (default), -m limit --limit 10/sec or custom, default: none | Set special SRC log options, e.g. to set a limit rate. |
| DST Log Options | -m limit --limit 2/sec (default), -m limit --limit 10/sec or custom, default: none | Set special DST log options, e.g. to set a limit rate. |
Advanced E-Mail Settings
| Name | Value | Description |
|---|---|---|
| E-Mail Sender Address | Sender address for banIP notification E-Mails. | |
| E-Mail Topic | string | Topic for banIP notification E-Mails. |
| E-Mail Profile | string | Profile used by 'msmtp' for banIP notification E-Mails. |
| E-Mail Actions | start, reload, restart or refresh, default: none | Limit E-Mail trigger to certain banIP actions. |
Blocklist Sources
In Blocklist Sources tab user can manage supported and fully pre-configured banIP sources. Section is divided into three parts: Country Selection, ASN Selection and Local Sources which are described in the table below.
| Name | Value | Description |
|---|---|---|
| Countries | ||
| ASNs | ||
| Local Sources | ||
| Extra Sources | ||
| Auto Blacklist | ||
| Auto Whitelist |
IPSet Report
This tab shows the last generated IPSet Report. Press the Refresh button to get a current one. To Search the active banIP-related IPSets for a specific IP, CIDR or MAC address press IPSet Querry button.
| Name | Value | Description |
|---|---|---|
| Timestamp | ||
| Number of all IPSets | number | |
| Number of all entries | number | |
| Number of IP entries | number | |
| Number of CIDR entries | number | |
| Number of MAC entries | number | |
| Number of accessed entries | number |
Edit Blacklist
This is the local banIP blacklist to always-deny certain IP/CIDR addresses. Note: add only one IPv4 address, IPv6 address or domain name per line. Comments introduced with '#' are allowed - wildcards and regex are not.
Edit Whitelist
This is the local banIP whitelist to always allow certain IP/CIDR addresses. Note: add only one IPv4 address, IPv6 address or domain name per line. Comments introduced with '#' are allowed - wildcards and regex are not.
Edit Maclist
This is the local banIP maclist to always-allow certain MAC addresses. Note: add only one MAC address per line. Comments introduced with '#' are allowed - domains, wildcards and regex are not.
Log View
The syslog output, pre-filtered for banIP related messages only.
[[Category:{{{model}}} User Manual]]