Elproma Smart Manager TLS
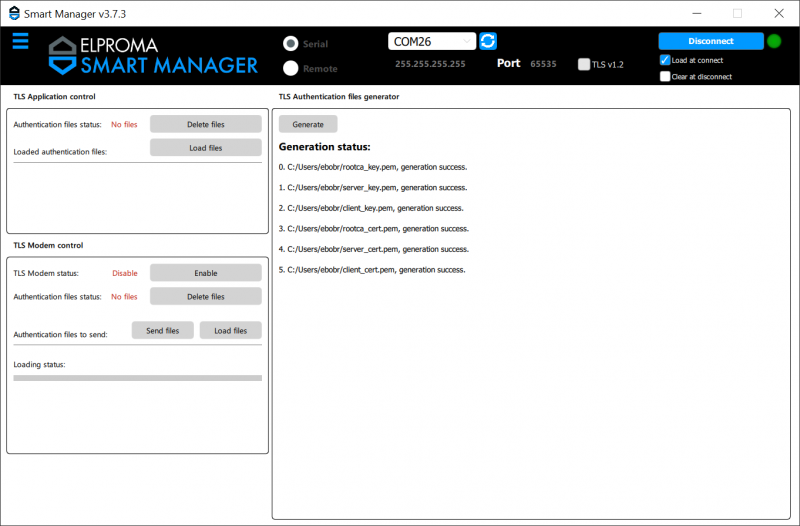
In the TLS window it is possible to configure the TLS communication mode of the modem. The modem in the network acts as the TLS server and the Elproma Smart Manager application acts as the client. In this window it is possible to upload keys and certificates for both server and client.
TLS client
The Elproma Smart Manager application acts as a client. In order to establish a connection between the modem and the application, it is necessary to load the key and certificate of the client and the certificate of the authorization center into the application. Required files:
- client_key.pem
- client_cert.pem
- rootca_cert.pem
Note: The file names of the keys and certificates must match those shown above, otherwise the files will not be loaded correctly into the application.
How to run the TLS client in the application?
1. In order to run it is necessary to prepare the files described in the Required files section. The files can be generated using the simple generator described in TLS Authentication files generator or using your own configuration tools (the only requirement is that the file names are consistent).
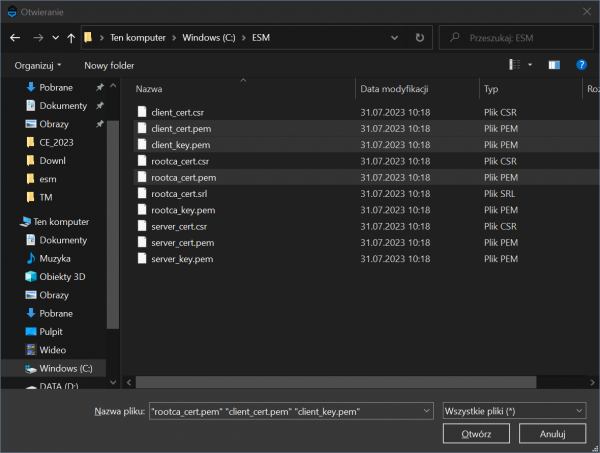
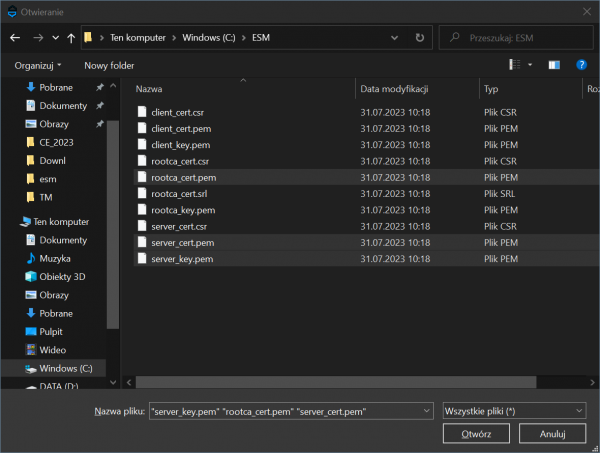
2. Load the keys and certificates into the application. To do this, click Load files button, which results in the opening of the file selection window. The files should be loaded all at once by multiple selection (to do this, hold down the CTRL key and select the necessary files).
3. Successful files importing results in the status of the authentication files changing to 'Loaded'.
4. In the final step, in order to enable the TLS module in the application, it is necessary to tick the "TLS v1.2" checkbox in the toolbar space.
5. It is now possible for the application to connect to the modem using TLS v1.2 encrypted communication.
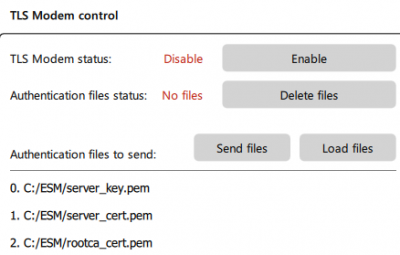
TLS Server
The RB900SG modem acts as a server. In order to establish a connection between the modem a nd the application, it is necessary to load the key and certificate of the client and the certificate of the authorization center into the modem.
Required files:
- server_key.pem
- server_cert.pem
- rootca_cert.pem
Note: The file names of the keys and certificates must match those shown above, otherwise the files will not be loaded correctly into the modem.
How to start the TLS server in the modem?
1. In order to run it is necessary to prepare the files described in the Required files section. The files can be generated using the simple generator described in TLS Authentication files generator or using your own configuration tools (the only requirement is that the file names must match).
2. Read the key and certificate files into the application using the Load Files button. The files should be loaded all at once by multiple selection (to do this, hold the CTRL key and select the necessary files).
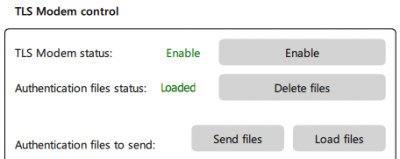
3. Once the files have been loaded into the application, they must be sent to the modem using the Send files button. Correctly uploading files to the modem will result in the status of the files changing to Uploaded.
4. In the last step, the TLS module in the modem must be enabled using the Enable button. Correctly enabling the TLS module on the modem will result in the modem status changing to Enabled.
TLS Authentication files generator
The file generator allows you to quickly and easily generate keys and certificates for both client and server. In order to generate these files, all you need to do is select the Generate button. The status and a list of the generated files with their exact paths will be displayed in the Generation status field. Once the files have been successfully generated, the application will automatically ask whether to load them into the application.
Note: The key and certificate file generator is a simple tool that is designed to quickly start the TLS module. The generator does not provide advanced configuration functions for the gen erated certificates/keys. The generated certificates are valid for 5 years.